What do you get when a fake author using a stolen identity publishes a gibberish-ridden novel on demand and then buys scads of them at high prices with dirty money? Clean money. h/t BoingBoing
Money Laundering Via Author Impersonation on Amazon?
Krebs on Security
February 20, 2018
Patrick Reames had no idea why Amazon.com sent him a 1099 form saying he’d made almost $24,000 selling books via Createspace, the company’s on-demand publishing arm. That is, until he searched the site for his name and discovered someone has been using it to peddle a $555 book that’s full of nothing but gibberish.
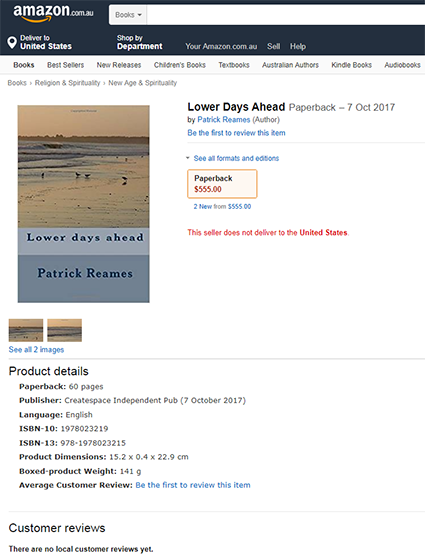
Reames is a credited author on Amazon by way of several commodity industry books, although none of them made anywhere near the amount Amazon is reporting to the Internal Revenue Service. Nor does he have a personal account with Createspace.
But that didn’t stop someone from publishing a “novel” under his name. That word is in quotations because the publication appears to be little more than computer-generated text, almost like the gibberish one might find in a spam email.
“Based on what I could see from the ‘sneak peak’ function, the book was nothing more than a computer generated ‘story’ with no structure, chapters or paragraphs — only lines of text with a carriage return after each sentence,” Reames said in an interview with KrebsOnSecurity.
The impersonator priced the book at $555 and it was posted to multiple Amazon sites in different countries. The book — which as been removed from most Amazon country pages as of a few days ago – is titled “Lower Days Ahead,” and was published on Oct 7, 2017.
Reames said he suspects someone has been buying the book using stolen credit and/or debit cards, and pocketing the 60 percent that Amazon gives to authors. At $555 a pop, it would only take approximately 70 sales over three months to rack up the earnings that Amazon said he made. Continue reading “A Novel Approach to Money Laundering”

 Critical fake comments, attributed to a real person, were reportedly posted against a controversial fiduciary rule to the Department of Labor”™s website, presumably to convince the department to do away with the rule altogether.
Critical fake comments, attributed to a real person, were reportedly posted against a controversial fiduciary rule to the Department of Labor”™s website, presumably to convince the department to do away with the rule altogether. In December 2015, readers at women”™s site xoJane were enthralled and filled with all-caps rage by Rachel Brewson, a self-described “giant liberal” who
In December 2015, readers at women”™s site xoJane were enthralled and filled with all-caps rage by Rachel Brewson, a self-described “giant liberal” who  …Part theater and part science, social engineering is the method by which hackers, for lack of a better term, exploit vulnerabilities in human psychology; for Jonah, it was a key to getting anything he wanted, from televisions and laptops to smartphones and expensive wines. One of his largest takes netted him around $60,000 worth of product, he says. He showed me a Rolex Daytona watch””part of a gallery of stolen goods he”™d photographed in his bedroom””which retails on
…Part theater and part science, social engineering is the method by which hackers, for lack of a better term, exploit vulnerabilities in human psychology; for Jonah, it was a key to getting anything he wanted, from televisions and laptops to smartphones and expensive wines. One of his largest takes netted him around $60,000 worth of product, he says. He showed me a Rolex Daytona watch””part of a gallery of stolen goods he”™d photographed in his bedroom””which retails on