The Kernel delves into the hidden subculture of liars, thieves, and hackers who expose and exploit gaping loopholes in e-commerce via Jonah (not his real name), someone who’s been there and back.
“Confessions of a social engineer”
by Dell Cameron
The Kernel
August 9, 2015
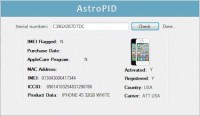 …Part theater and part science, social engineering is the method by which hackers, for lack of a better term, exploit vulnerabilities in human psychology; for Jonah, it was a key to getting anything he wanted, from televisions and laptops to smartphones and expensive wines. One of his largest takes netted him around $60,000 worth of product, he says. He showed me a Rolex Daytona watch””part of a gallery of stolen goods he”™d photographed in his bedroom””which retails on Amazon for around $26,000.
…Part theater and part science, social engineering is the method by which hackers, for lack of a better term, exploit vulnerabilities in human psychology; for Jonah, it was a key to getting anything he wanted, from televisions and laptops to smartphones and expensive wines. One of his largest takes netted him around $60,000 worth of product, he says. He showed me a Rolex Daytona watch””part of a gallery of stolen goods he”™d photographed in his bedroom””which retails on Amazon for around $26,000.
Whether through face-to-face interaction, by phone, or by email, the human gatekeepers of any network can be exploited””if you know how to play the game. They”™re the weakest link in any company”™s security.
Almost every major electronics company is vulnerable in nearly the same way: They all have warranty-based replacement systems that can be exploited. Most companies, for instance, don”™t require a defective item to be returned before mailing out its replacement. It”™s likewise difficult to prove that an in-warranty item has been lost or stolen.
Through repeated phone calls, social engineers develop strategies for navigating a company”™s customer help line. They get a feel for which sob stories and which “yes” or “no” responses will work best toward achieving their objective. Intelligence, temperament, and even humor all come into play. The questions and responses are then mapped out, as if composing a flowchart, with the goal of expediting the con. Read the whole article.
